Sublime
An inspiration engine for ideas

China employs a “whole of society” approach to espionage, using both its intelligence services, as well as purportedly private Chinese companies, Chinese nationals, and diaspora communities. China’s strategy is to overwhelm Western counterintelligence, if not through sophisticated espionage tradecraft, then by volume.
Calder Walton • Spies: The Epic Intelligence War Between East and West
AgentPlatformsW97.PDF
cis.upenn.eduOthman was the director of the Syrian Atomic Energy Commission.
Ronen Bergman • Rise and Kill First: The Secret History of Israel's Targeted Assassinations
However, these systems have an unfortunate tendency to concentrate power often excessively,
Audrey Tang • ⿻ 數位 Plurality: The Future of Collaborative Technology and Democracy

Jonathan Powell, presently National Security Advisor, gave a fairly simple solution to Blair twenty years ago on the asylum question. https://t.co/9krE0YyCLn
C'est très certainement le média le mieux informé sur ces arcanes du pouvoir et du renseignement français, et si vous n'avez pas d'abonnement pour lire toute la série d'articles sur le renseignement sous Macron, je crois qu'on fait vraiment le tour dans cet épisode. https://t.co/ZB8YFILPpH
Alexandre Jubelinx.comHere is Larry Ellison talking to Tony Blair at the World Government Summit 2025.
He describes how all data (health, finance, genomic) needs to be centralized before AI can be deployed to enforce control. https://t.co/DQ2281oUPB
Harrison H. Smith ✞x.com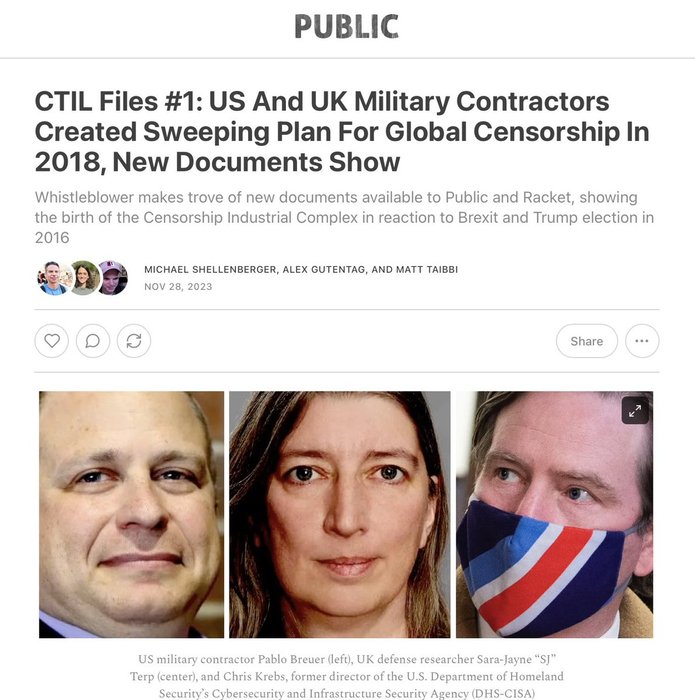
THE CTIL FILES #1
Many people insist that governments aren't involved in censorship, but they are. And now, a whistleblower has come forward with an explosive new trove of documents, rivaling or exceeding the Twitter Files and Facebook Files in scale and importance. https://t.co/tqgSQjPIuT