Sublime
An inspiration engine for ideas
Digital Society
Grit Wolany • 1 card
Digital Self
Joe Maceda • 6 cards
Cybersecurity
Carmen • 1 card
AI billionaire’s advice to teens: Master 'vibe coding' — here’s 5 prompts to get started
share.google
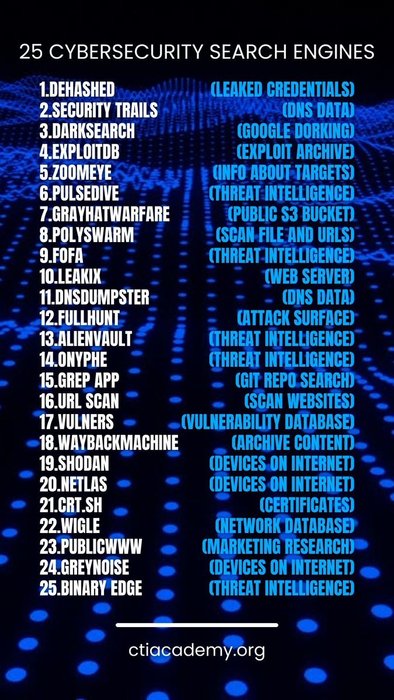
Top 25 Cyber Security Search Engines
#cybersecurity #infosec https://t.co/xpGoKLQowD
Computers
Jonathon Yule • 4 cards