Saved by Chad Hudson
OSINT for Incident Response
OSINTMAILER - is a robust Python-based open-source intelligence (OSINT) tool specifically designed to validate and investigate email addresses by gathering publicly available information across various online platforms and data breach databases.
#OSINT
#Cybersecurity https://t.co/pdx6nB2Buz
D4rk_Intelx.comOSINTMAILER - is a robust Python-based open-source intelligence (OSINT) tool specifically designed to validate and investigate email addresses by gathering publicly available information across various online platforms and data breach databases.
#OSINT
#Cybersecurity https://t.co/pdx6nB2Buz
Tech Enthusiastx.com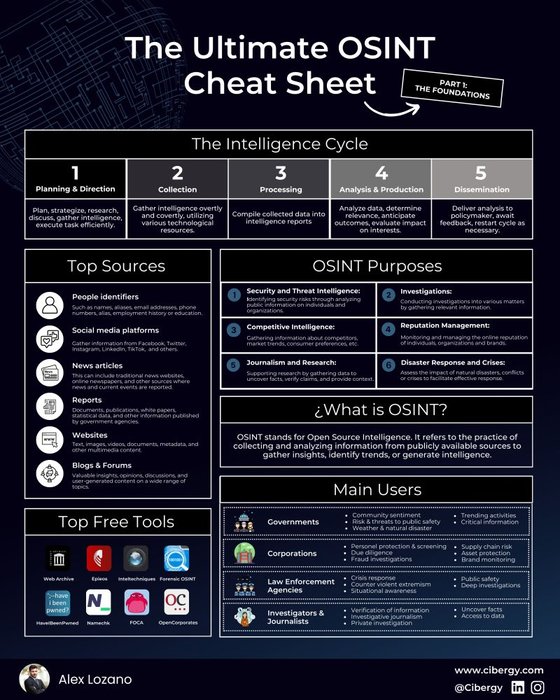
The Ultimate OSINT Cheat Sheet
#cybersecurity #infosec #OSINT https://t.co/XZUgmhoW4A