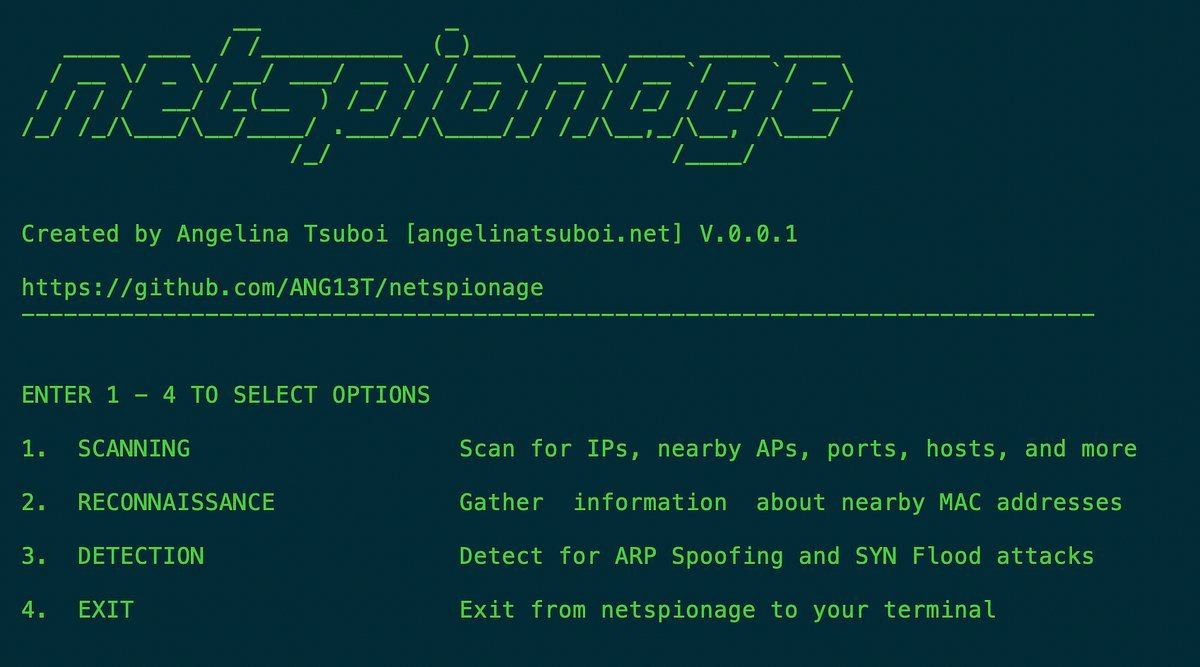
netspionage: Network Forensics CLI utility that performs Network Scanning, OSINT, and Attack Detection
GitHub: https://t.co/wJQIHZxgjw https://t.co/vUNnCEwIlE
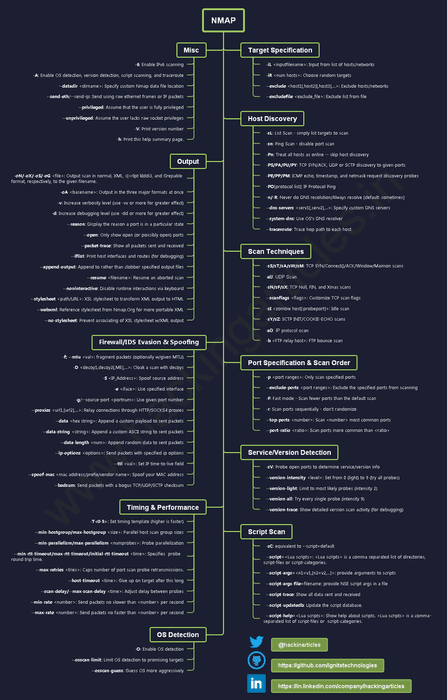
Nmap for Pentester
✴ Link: https://t.co/d1tXtSq381
This cheat sheet was created to assist Red Teamers and Penetration Testers in hunting down vulnerabilities using "Nmap."
🛑 Host Discovery
🛑Output Format Scan
🛑Nmap Packet... See more

