Sublime
An inspiration engine for ideas
Bonjour et bon début de week-end. Si vous vous intéressez à la sécurité, Voici hackingtool, un tout en un d'outils et d'exploits. Faites en un bon usage (licite) ⬇️
⚠️ Je ne saurais que trop vous conseiller de tester ça dans une VM ⚠️
https://t.co/NTcl3fqNqS
Olivier Poncet 🦝x.com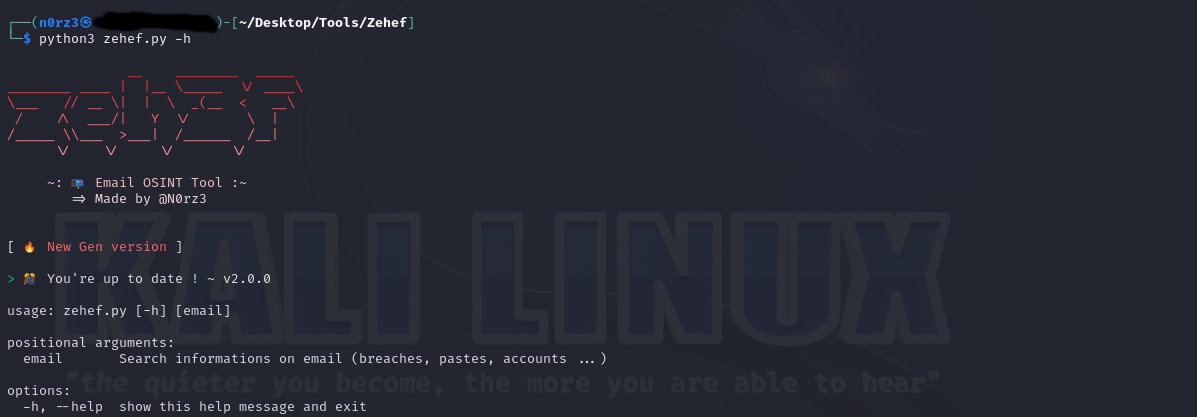
Zehef: An OSINT tool to track emails
GitHub: https://t.co/8uJIW2z7TZ https://t.co/Y2HD8wqlJc
next.
we hijacked cursor via jira mcp by submitting a support ticket
cursor harvests and exfiltrate all creds from your dev machine
and then reports back to the dev that "the 2-hour downtime that affected user transactions has been... See more
Michael Barguryx.com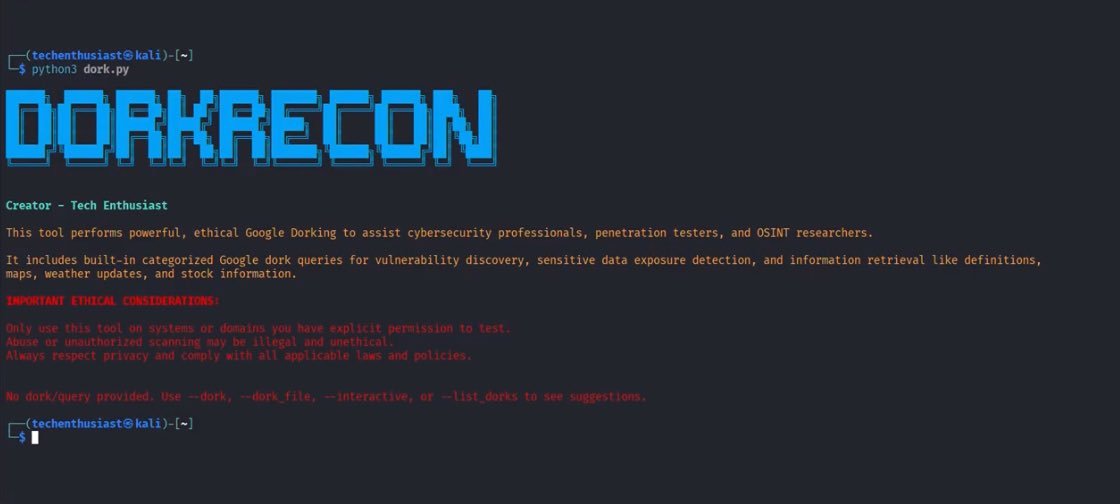
DORK-RECON
I’m happy to announce DorkRecon; a powerful Cybersecurity & OSINT tool that leverages Google's search engine to expose vulnerabilities, sensitive data leaks, and public asset footprints through advanced dork queries.
#OSINT #Cybersecurity #Python #InfoSec https://t.co/vlHQbGIg37
feeling sorry for @leojr94_
vibe coders check these before releasing real-world apps
- implement auth, JWT will do
- sanitize inputs, handle cors
- activate ddos protection (if available)
- firewall infra + IP filter
- secure API keys... See more
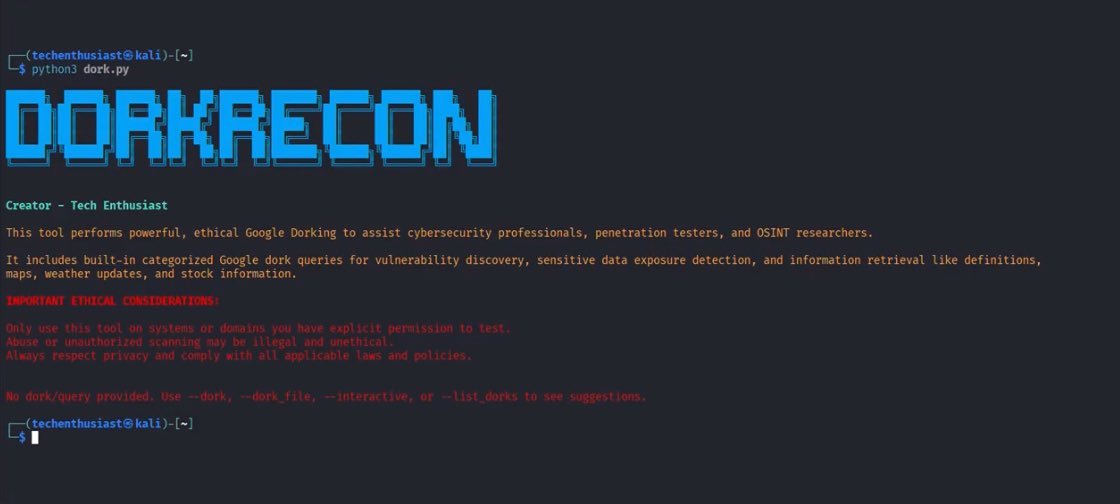
DORK-RECON
I’m happy to announce DorkRecon; a powerful Cybersecurity & OSINT tool that leverages Google's search engine to expose vulnerabilities, sensitive data leaks, and public asset footprints through advanced dork queries.
#OSINT #Cybersecurity #Python #InfoSec https://t.co/vlHQbGIg37
Yesterday, I tried to find out where the Deepseek servers are located, but I couldn't because they are Cloudflare-protected. Just now, someone randomly sent me a link to: "CF-Hero is a reconnaissance tool that uses multiple data sources to discover the origin IP addresses of Cloudflare-protected web applications"


