Sublime
An inspiration engine for ideas
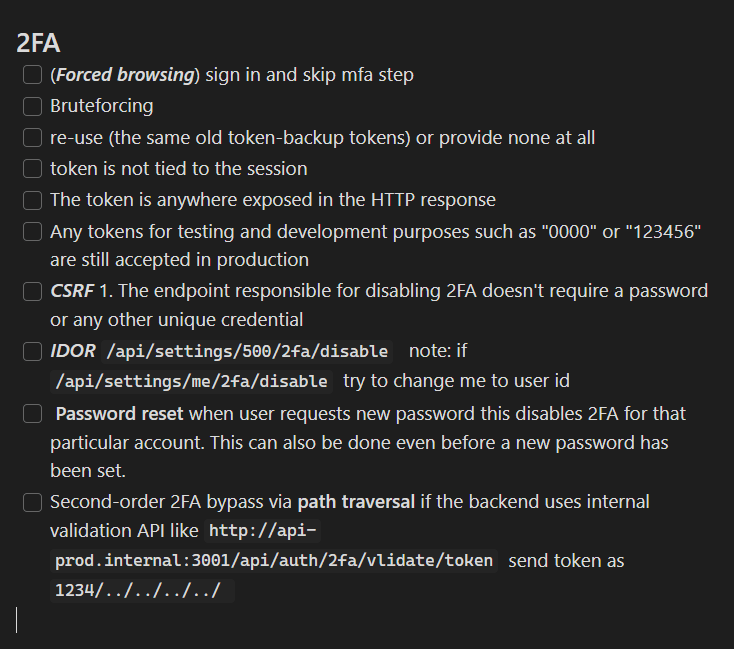
SIM SWAPPER’S DELIGHT
JackieChan is most active on Telegram channels focused on “ SIM swapping ,” which involves bribing or tricking mobile phone company employees into redirecting a target’s phone number to a device the attackers control. SIM swapping allows crooks to temporarily intercept the target’s text messages and phone calls, including any
... See moreBrianKrebs • ID Theft Service Resold Access to USInfoSearch Data
I worked directly on DPRK's biggest bridge hack ever (Ronin), helped track BSC bridge hackers off-chain, and was at Apple in the security team at the time of the Pegasus spyware so I consider myself somewhat of an expert here. I'd recommend the
team to do the following asap: 1) Hop on a call with
2) Get new laptops + ledgers
... See moreSo I found a ZERO-CLICK vulnerability in @argentHQ allowing an attacker to steal all the funds out of all wallets without any user action or interaction ☠️
Just iterate over wallets and steal funds, easiest 💰
Now that user funds are safe, I can share the story 👇
Yoav Gazielx.com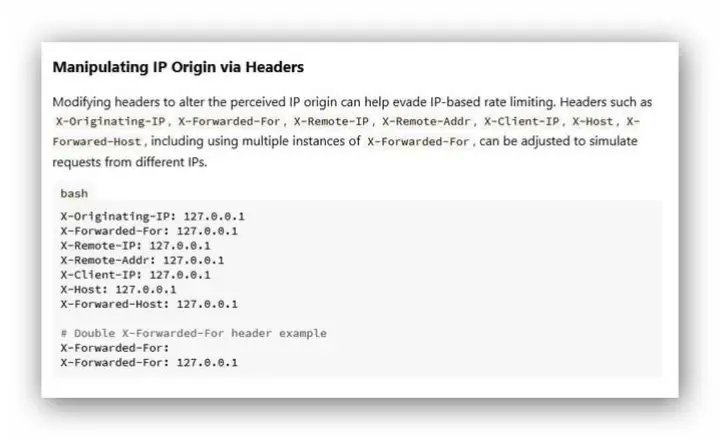
Rate limit bypass techniques
X-Originating-IP: 127.0.0.1
X-Forwarded-For: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
X-Client-IP: 127.0.0.1
X-Host: 127.0.0.1
X-Forwared-Host: 127.0.0.1
Sigue... See more
INTRODUCING: Agentic Security - LLM Security Scanner! 🔍
🔑 Features:
Scans for prompt injections, jailbreaking & more.
Provides detailed reports & options to customize attack rules.
🔗access the GitHub Link ↓
Alexander Miax.com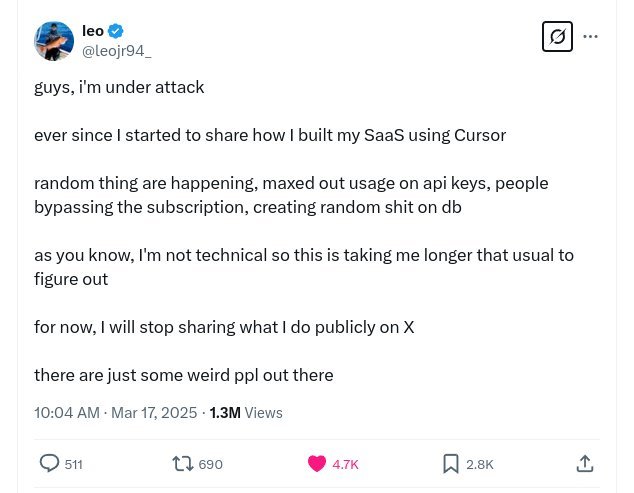
feeling sorry for @leojr94_
vibe coders check these before releasing real-world apps
- implement auth, JWT will do
- sanitize inputs, handle cors
- activate ddos protection (if available)
- firewall infra + IP filter
- secure API keys... See more