Sublime
An inspiration engine for ideas
Valuables by Cent.
Crypto Dukedom • The NFT Revolution 2021
Identity
Juniper • 7 cards
Curation
Linda Tong • 1 card
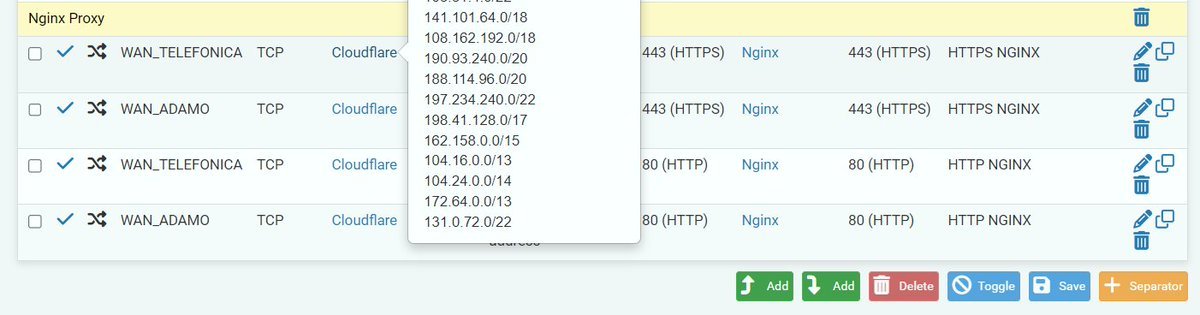
Un dominio que tiene un proxy en @Cloudflare apuntando a mi IP (Así al resolver el dominio sólo aparece la ip de cloudflare no la mia) donde le espera otro proxy @nginx apuntando a la MV interior que da servicio X. Todo esto con SSL Let's Enctrypt y sólo aceptando las ips deCloudflare para dar acceso al puerto 443 y 80 dentro de Pfsense.... See more
Identity
Leela R Sinha • 5 cards
Cyber Security
Calvin Fuller • 2 cards

