Sublime
An inspiration engine for ideas
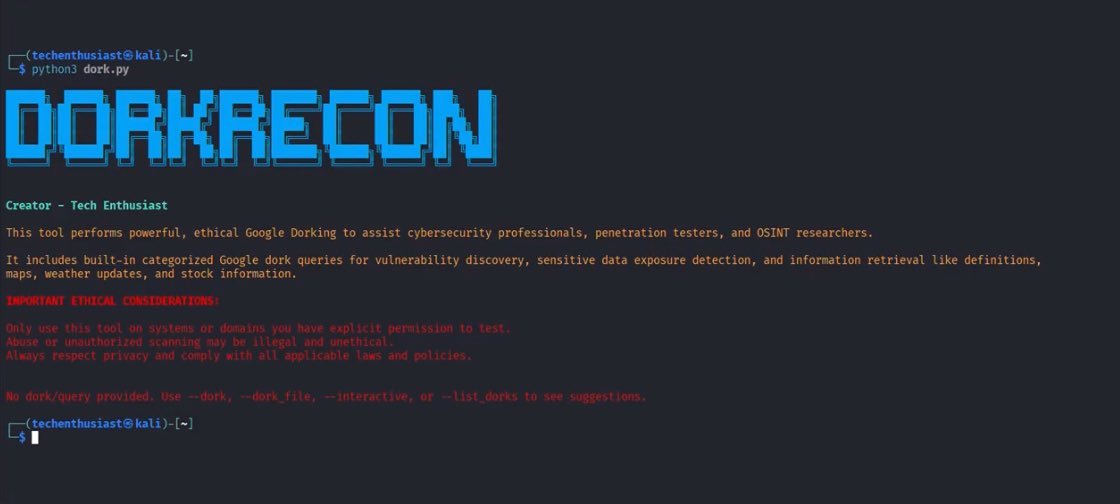
DORK-RECON
I’m happy to announce DorkRecon; a powerful Cybersecurity & OSINT tool that leverages Google's search engine to expose vulnerabilities, sensitive data leaks, and public asset footprints through advanced dork queries.
#OSINT #Cybersecurity #Python #InfoSec https://t.co/vlHQbGIg37
"Bjorn is a powerful network scanning and offensive security tool for the Raspberry Pi with a 2.13-inch e-Paper HAT. It discovers network targets, identifies open ports, exposed services, and potential vulnerabilities. Bjorn can perform brute force attacks, file stealing, host zombification, and supports custom attack scripts."
Introducing Dork-Recon: a powerful tool with categorized dork sets for common vulnerabilities and OSINT data - including WordPress, credentials, cameras, login portals, and more. Features interactive mode, bulk search, and safe search for efficient reconnaissance.
#Cybersecurity https://t.co/tcRfeUZJgp
Tech Enthusiastx.com


