Sublime
An inspiration engine for ideas
The way the tech works is exceptionally cool. If you own an Anata, you can verify it in your wallet with their browser plugin. Then whenever you open a video conferencing tool like Google Meet, you can choose to have your Anata take over your video stream instead of your webcam. The Anata is stored on Arweave and streams from there, so you don't... See more
Nat Eliason • From PFPs to VIDs
Hacks
Madeleine Webb • 1 card
There were two main aspects of the LulzSec arrests the Feds needed to pull off for the takedown to work properly. First, it was imperative that they capture every suspect at the exact same time, even though they were all in different states and countries. They had to ensure that the hackers didn’t alert anyone else about their arrests, or the
... See moreNick Bilton • American Kingpin: Catching the Billion-Dollar Baron of the Dark Web
privacy (ZK, TEE, etc)
Zeebra doom • 4 cards
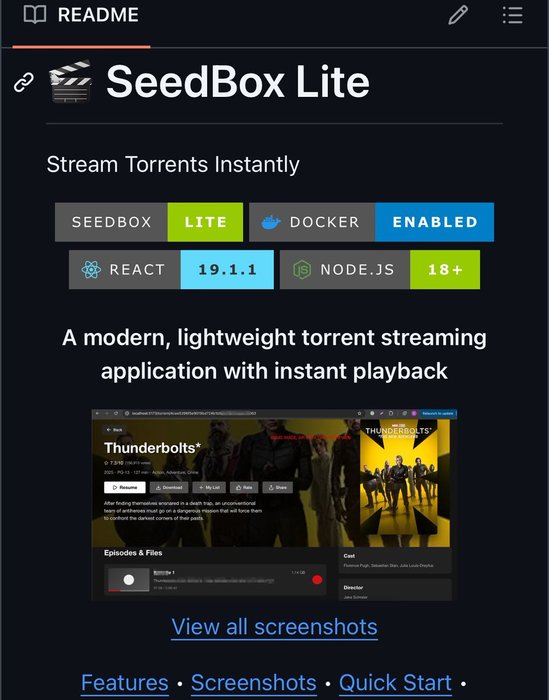
Open-source, modern, lightweight torrent streaming application with instant playback. https://t.co/A7yF56cGIT