Sublime
An inspiration engine for ideas
trust
Linkalier • 2 cards
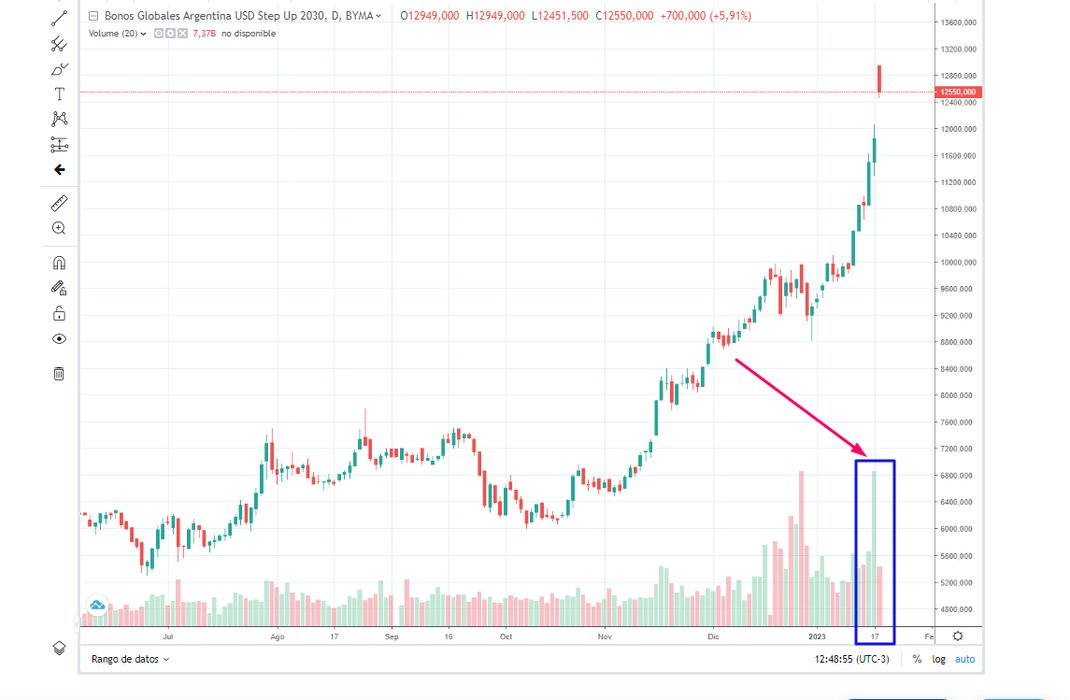
Ayer el Bono q hoy @SergioMassa anunció que va a recomprar operó su máximo volumen histórico.
Traduzco: el criminal que oficia de Ministro d Economía le avisó a sus amigos lo q pensaba hacer
Si qeres comprar algo, lo compras primero y lo anuncias después. Nunca antes, a menos q.. https://t.co/aBEfFexLY3
money & markets
Ishan Sinha Marjit • 12 cards
Commerce
Joe Maceda • 1 card
crypto history
Tekelala and • 10 cards
Smart Contracts
Maria Carolina Suarez • 1 card

